Stop worrying about employees copy-pasting code into ChatGPT. Start worrying about autonomous agents logging into your production environment.
I’ve been thinking a lot about our security blind spots lately. While we focus on data leakage, we are overlooking the massive shift occurring in our infrastructure: AI is no longer just a tool we wield; it is becoming an actor that acts on its own.
To survive the agentic wave, stop treating agents as tools. Instead, treat them as first-class identities—independent actors in their own right.
In this issue, I want to challenge you to look at your IAM strategy through this new lens. If your security stack can’t distinguish between a human and an agent, you might be more exposed than you think.
Let’s dig in.
The Shift: From Chatbots to Shadow Identities
In 2024, our biggest fear was "Shadow AI"—employees leaking proprietary code into a browser-based LLM. We handled that with DLP tools and corporate licenses.
In 2025, the risk has evolved from what employees type to what their autonomous agents execute. We have entered the era of the "Shadow Identity," where agents act as non-human users, often piggybacking on over-privileged service accounts to move data or modify infrastructure.
The danger isn't just data leakage; it’s non-deterministic action. If an agent has "God-mode" access to your GitHub or AWS environment to "help with DevOps," a single hallucination can lead to a production wipeout.
Why Your Current IAM is Blind
Traditional Identity and Access Management (IAM) was built for two things: humans behind a browser and static service-to-service communication. AI agents fit neither category.
Agents are dynamic, non-deterministic, and capable of chain-of-thought execution. When an agent uses a generic "Dev-Service-Account" token, your logs show authorized activity, but your governance layer has zero visibility into the intent behind the call.
We must move from "Who is accessing this?" to "Which agent is acting on whose behalf, and does this action match its reasoning scope?"
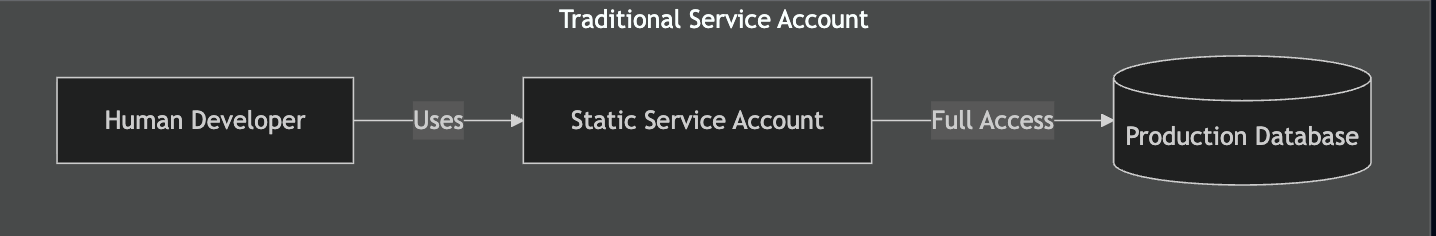
Traditional Service Account Flow
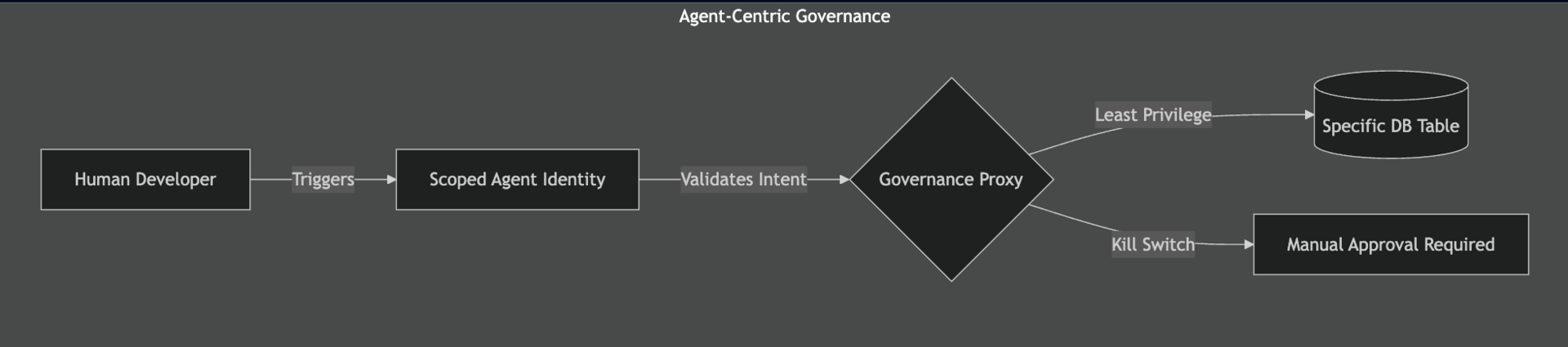
Agent-Centric Governance with a policy following least Privilege
The Strategy: Agent-Centric Identity Governance
To survive the agentic wave, stop treating agents as tools. Instead, treat them as first-class identities—as independent actors
First, decouple agents from general service accounts. Every autonomous agent should have its own unique Identity Provider (IdP) entry. If "Agent Alpha" is responsible for Jira automation, it should never share a token with "Agent Beta" which handles CI/CD.
Second, Use Short-Lived, Scoped Tokens. Agents should never hold long-lived credentials. Use OIDC (OpenID Connect) to exchange agent identity for ephemeral tokens that expire the moment the specific task is complete.
Third, build the "Agent Kill Switch." This isn't just a "Revoke" button in IAM. It’s a programmatic guardrail that monitors for non-deterministic behavior—like an agent suddenly trying to export a database when its task was only to update a schema. ---
From the Trenches
The Tactic: Use AWS IAM Session Tags to track agentic intent. By tagging the session at the moment of assume-role, you create a cryptographic link between a specific AI task ID and the API calls it makes.
The Policy (Example Service Control Policy):
{ "Version": "2012-10-17", "Statement": [ { "Sid": "EnforceAgentTagging", "Effect": "Deny", "Action": "sts:AssumeRole", "Resource": "*", "Condition": { "Null": { "aws:RequestTag/AgentID": "true" } } } ] }The Governance Check
The Risk: Shared API keys in environment variables being scraped by "helpful" coding agents and stored in their own memory or vector databases.
The Fix: Transition all agentic connections to Workload Identity Federation. Ensure no agent ever "sees" a secret; they should only ever exchange a signed JWT for a temporary session. If an agent can read the secret, so can the hallucination.
How many autonomous agents (not just chatbots) are currently hitting your internal APIs?
P.S. Need help locking down your infrastructure? I opened up 2 slots for a Strategic AI Architecture Review to help you start 2026 fresh.